Avoid Fraudulent Purchases
Challenge
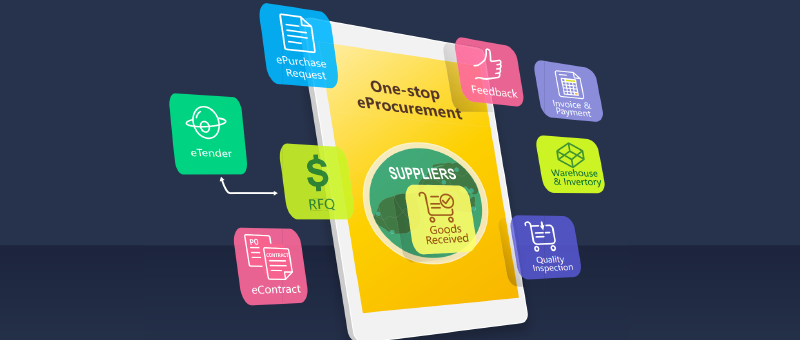
Procurement is purchasing goods and services for an organization, and most business expenditures flow through departments. The procurement department is responsible for negotiating contracts and procuring the goods and services required by the business. The sourcing and procurement process is particularly prone to fraud and difficult to detect, especially in large organizations with complex procurement operations.

The goal of a good procurement strategy is to source the best possible goods and services at the lowest possible price while reducing risk, building strong relationships with trusted supplier partners as well as taking advantage of cost-saving opportunities and ensuring a smooth payment process. Procurement fraud can take many forms, from embezzlement to overpriced items. Below are some of the most common types of fraud whereby employees defraud an organization of funds.
1. Rebate
One of the most common frauds is rebates or rewards. Suppliers pay rebates to the buyer who purchases goods and services. The rewards may be cash payments, benefits, influence or other forms of bribes.
To earn rebates, purchasing managers may approve substandard suppliers, procure unnecessary goods or services, or disrupt the tender process by excluding preferred suppliers. Another common strategy is to write project specifications in such a way that only one bidder can qualify.
Bribery-based transactions are rarely beneficial to the purchasing organization. Suppliers may overcharge or provide inferior products to recoup bribes. Even if the product is acceptable and reasonably priced, the purchasing organization will lose the competitive advantage.
2. Conflicts of Interest
Another common fraud involves undisclosed relationships with bidding companies. For example, the person who ultimately approves the bidding process may own stock in the winning company or have some relationship with the company or its shareholders. Since the employee profits indirectly from the transaction, his interest is in making the best deal for the supplier, which often means a bad deal for the organization that pays him.
Because procurement is a complex operation involving large sums of money and multiple contractors, it is highly susceptible to fraudulent schemes.
3. Fake company/order
One of the most shocking and easily detected procurement fraud schemes is the simple manipulation of the system by submitting orders to shell companies and invoicing products that are never received. This type of fraudulent scheme seems unlikely to work, but it is easy to implement in an organization with fragmented procurement and disorganized processes, especially if there is no procurement software available to verify orders from purchase order to delivery, invoice and payment.
In order to process false or fraudulent orders under the company’s watch, employees may place a series of small orders that do not require formal bidding or approval. Certain types of purchases or exceeding set amounts may trigger contract approval thresholds. By making fake orders small enough for expected items to bypass the approval requirement process, employees can successfully commit fraud, at least for a while.
4. Fraudulent Invoices
Procurement fraud does not always happen internally. Suppliers may invoice undelivered inventory items, submit duplicate invoices, or charge fees in excess of the negotiated contract amount, or substitute lower-quality materials, or charge for work that was never performed.
5. Bid rigging
A group of suppliers has been known to conspire to inflate prices during the bidding process. Bid rigging is a situation where a group of suppliers submits high prices to benefit a particular bidder. Typically, in this case, the winning bidder and the losing competitors profit from inflating the contract price.
Solution
The main weapon in any fraud prevention toolbox is procurement software. Distinguishing patterns and trends might be difficult for humans. However,  SRM software can easily handle them in seconds. It can build custom reports to flag abnormal expenditures and build and audit trails for three-way matching between purchase orders, delivery notes and invoices to ensure that companies pay only verified invoices and not duplicate invoices. A comprehensive procurement program monitors compliance issues, stores current price lists for comparison, and tracks reviewed supplier information.
SRM software can easily handle them in seconds. It can build custom reports to flag abnormal expenditures and build and audit trails for three-way matching between purchase orders, delivery notes and invoices to ensure that companies pay only verified invoices and not duplicate invoices. A comprehensive procurement program monitors compliance issues, stores current price lists for comparison, and tracks reviewed supplier information.
Spotting fraud does not always require a certified fraud examiner. Fraudulent schemes can often be detected through unexpected employee behavior, including:
- Lack of focus on quality standards. If the quality of goods and services is questioned and procurement officials ignore or justify the complaint, there may be a problem.
- If an invoice reflects a price that is significantly higher than the negotiated contract price, previous contracts, or industry standards, the contract may not be legal.
- Use the same supplier and refuse to consider other bids. If a purchasing manager is defending a supplier that clearly does not meet company standards or competitive prices, consider hiring a fraud examiner to conduct a contract audit.
- Limit communication with preferred suppliers. A single point of contact with a supplier is suspicious and may indicate an improper relationship.
The following are early warning signs of possible bid-rigging:
- The winning bid was significantly higher than expected based on estimates, company price lists or previous contracts.
- Winning bidders in the same group rotate by job, job type or location
- Lost bidders in the same project were hired as subcontractors
- Unusual bidding patterns; similar high bids with lower outliers, similar integers
- Incomplete or sloppy bids, identical bids from different companies
Using software that includes an automatic audit trail (electronic trail), such as  SRM, you will be more likely to detect suspicious behavior.
SRM, you will be more likely to detect suspicious behavior.
Use  SRM to gain a clear centralized procurement process and reduce room for fraud:
SRM to gain a clear centralized procurement process and reduce room for fraud:
- Purchasing contracts should be checked and balanced. Purchasing managers or department managers should not be the only approvers. Bulk purchases require approval from a higher-level manager.
-
Management and employees should be trained and encouraged to be aware of the red flags of the
 SRM system, which can greatly increase the chances of detecting a corrupt scheme.
SRM system, which can greatly increase the chances of detecting a corrupt scheme.
-
Leverage
 SRM to implement an automatic three-party matching system to validate invoices before payment.
SRM to implement an automatic three-party matching system to validate invoices before payment.
-
Leverage
 SRM to clearly define and enforce tender terms and acceptance requirements.
SRM to clearly define and enforce tender terms and acceptance requirements.
-
Ensure supplier due diligence is performed during the supplier approval process. Suppliers shall be thoroughly reviewed and verified by at least two persons and kept in the
 SRM Supplier Database.
SRM Supplier Database.
-
Run expense analysis reports regularly with
 SRM to identify over-consumption or maverick spending.
SRM to identify over-consumption or maverick spending.
Procurement fraud can and does happen to the world’s largest companies. The key to prevention lies in understanding data, changes in market pricing and purchasing patterns.  SRM makes all functions easier.
SRM makes all functions easier.