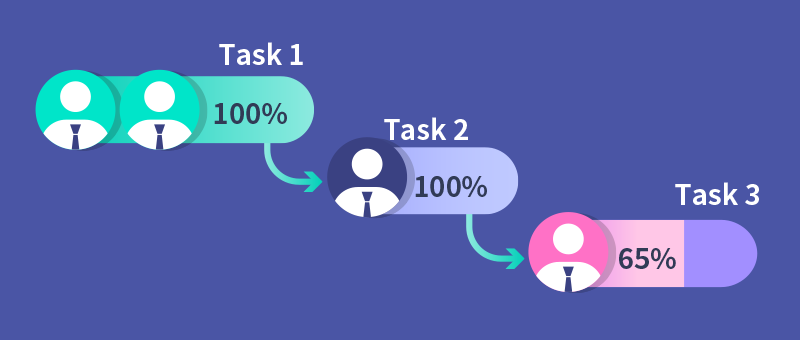
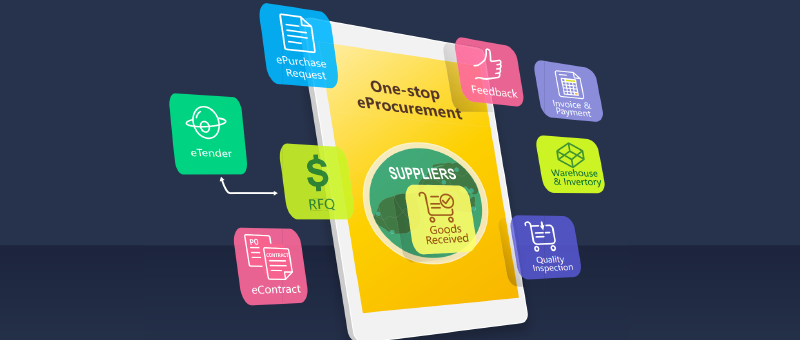
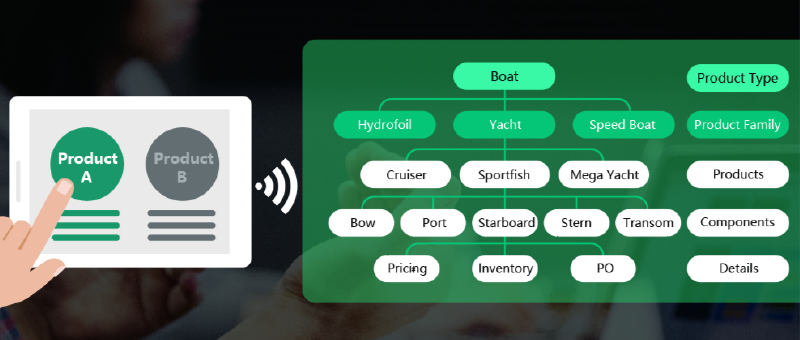
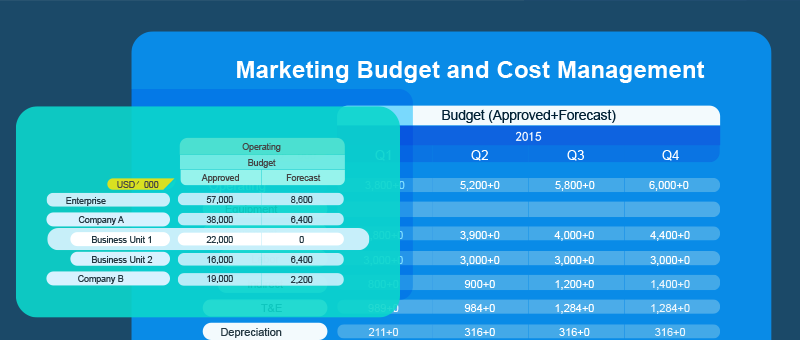
Advanced IT operations
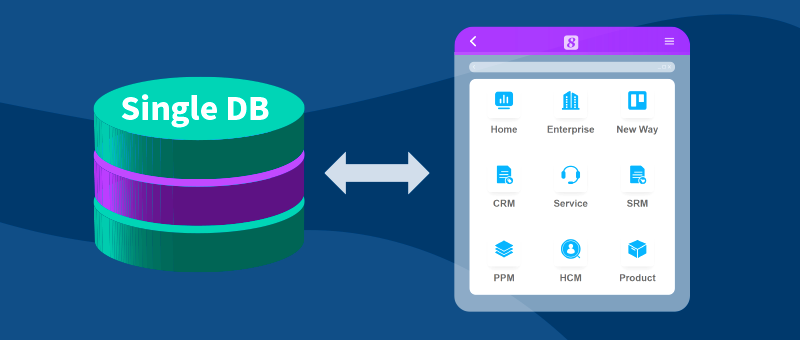
Over 500 corporations have used  enterprise applications to transition their business process
enterprise applications to transition their business process
and data management to cloud and empowered their employees to respond rapidly to emerging trends and customer needs.
 enterprise applications to transition their business process
enterprise applications to transition their business processand data management to cloud and empowered their employees to respond rapidly to emerging trends and customer needs.



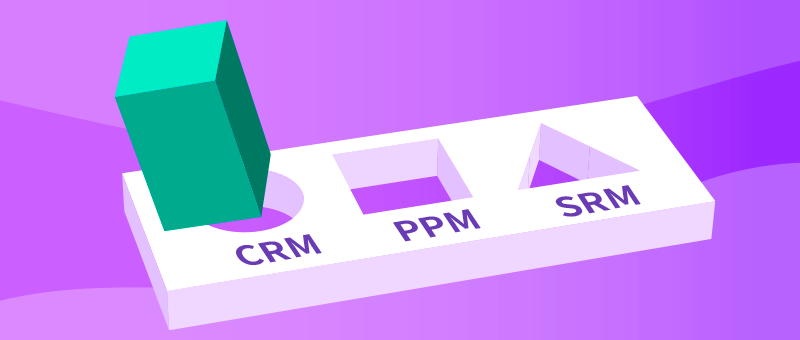
Application Customization
 Advanced SaaS allows application customizations provided by us or done by our customers using
Advanced SaaS allows application customizations provided by us or done by our customers using  SDK. The types of customizations can range from development of interfaces to external systems, minor customization for changing
SDK. The types of customizations can range from development of interfaces to external systems, minor customization for changing  application behaviors to major customization such as adding new application modules to
application behaviors to major customization such as adding new application modules to  .
.
Web Accelerator
 Web Accelerator relies on BGP bandwidth and the global transmission network to achieve local access to the global network, which can reduce the impact of network problems such as latency, jitter, and packet loss on service quality, and provide high-availability and high-performance network acceleration services to global users.
Web Accelerator relies on BGP bandwidth and the global transmission network to achieve local access to the global network, which can reduce the impact of network problems such as latency, jitter, and packet loss on service quality, and provide high-availability and high-performance network acceleration services to global users.
Hardware Hot Failover
The system design of  Advanced SaaS allows adding extra hardware as hot standby to compensate for hardware failures. The goal is to ensure that
Advanced SaaS allows adding extra hardware as hot standby to compensate for hardware failures. The goal is to ensure that  Advanced SaaS remains functional and avoid downtime because of network equipment, server hardware or storage hardware failure.
Advanced SaaS remains functional and avoid downtime because of network equipment, server hardware or storage hardware failure.
 Advanced SaaS allows adding extra hardware as hot standby to compensate for hardware failures. The goal is to ensure that
Advanced SaaS allows adding extra hardware as hot standby to compensate for hardware failures. The goal is to ensure that  Advanced SaaS remains functional and avoid downtime because of network equipment, server hardware or storage hardware failure.
Advanced SaaS remains functional and avoid downtime because of network equipment, server hardware or storage hardware failure.
Short Recovery
 Short Recovery (RPO & RTO) means that in the event of a disaster,
Short Recovery (RPO & RTO) means that in the event of a disaster,  Advanced SaaS can recover more quickly and minimize data loss, making it suitable for businesses that need high business continuity and high data integrity.
Advanced SaaS can recover more quickly and minimize data loss, making it suitable for businesses that need high business continuity and high data integrity.
 Advanced SaaS has the following recovery objectives:
Advanced SaaS has the following recovery objectives:
- Recovery Point Objective (RPO) is less than 4 hours
- Recovery Time Objective (RTO) is less than 4 hours
IaaS & PaaS
 Infrastructure as a Service (IaaS) provides on-demand access to the basic building blocks of cloud IT, such as networking, storage, and virtual or dedicated hardware computers.
Infrastructure as a Service (IaaS) provides on-demand access to the basic building blocks of cloud IT, such as networking, storage, and virtual or dedicated hardware computers.
 Platform as a Service (PaaS) provides hardware and software resources, such as an operating system,
databases, programming language execution environment, web server running and managing
applications.
Platform as a Service (PaaS) provides hardware and software resources, such as an operating system,
databases, programming language execution environment, web server running and managing
applications.
Firewall
 Firewall monitors and controls network traffic to prevent unauthorized access to your computer or network. It acts as a barrier between your network and an untrusted outside network. Web Application Firewall (WAF) is a security defense that protects websites, mobile applications, and APIs from threats by monitoring, filtering, and blocking data packets. WAF was designed to detect and protect against common security flaws in web traffic. It can help protect against malicious attacks and unwanted internet traffic, including bots, injection, and application-layer Denial of Service (DoS).
Firewall monitors and controls network traffic to prevent unauthorized access to your computer or network. It acts as a barrier between your network and an untrusted outside network. Web Application Firewall (WAF) is a security defense that protects websites, mobile applications, and APIs from threats by monitoring, filtering, and blocking data packets. WAF was designed to detect and protect against common security flaws in web traffic. It can help protect against malicious attacks and unwanted internet traffic, including bots, injection, and application-layer Denial of Service (DoS).
Additional Security
Hypertext transfer protocol secure (HTTPS) is used to protect data transfer between a user and your server by encrypting all data in transit. This is especially important when users are transmitting sensitive data, such as personal and financial information. HTTPS ensures that no third parties can intercept the data over the network, and that the data has not been tampered with or modified.
 Two-factor authentication (2FA) is used as an identity and access management security method that requires two forms of identification to access resources and data.
Two-factor authentication (2FA) is used as an identity and access management security method that requires two forms of identification to access resources and data.  2FA gives your business and operations the ability to monitor and help safeguard their most vulnerable information and networks.
2FA gives your business and operations the ability to monitor and help safeguard their most vulnerable information and networks.
Advanced Encryption Standard (AES) 256 is used for file and database encryptions, Secure Hash Algorithm (SHA) 256 is used for password hashing and Pretty Good Privacy (PGP) 4096 is used for license file encryptions.
Certification
ISO27001 is an international standard that helps establish, maintain, and improve information security management systems (ISMS). The ISMS is a set of policies and procedures that outline how an organization's processes protect its data. The standard is used by companies of all sizes and from all sectors of activity.
ISO9001 is defined as a set of international standards on quality management and quality assurance developed to help organizations manage quality and ensure they meet customer expectations.
ISO9001 is defined as a set of international standards on quality management and quality assurance developed to help organizations manage quality and ensure they meet customer expectations.
Application Installation
 Application installation service includes installation and testing of the applications, middleware and proxy servers to make them ready for execution.
Application installation service includes installation and testing of the applications, middleware and proxy servers to make them ready for execution. Application installation service also include middleware and application version upgrades and patch installations for applications, proxy servers, middleware, DBMS and OS.
Application installation service also include middleware and application version upgrades and patch installations for applications, proxy servers, middleware, DBMS and OS.
OOTB Data Initialization
 OOTB data initialization service includes initialization of all the default code tables, policies and flows so that the system administrator can further customize them for specific needs.
OOTB data initialization service includes initialization of all the default code tables, policies and flows so that the system administrator can further customize them for specific needs.
Vulnerability Scan
 Vulnerability scanning service is used for identifying and evaluating security flaws in applications and underlying systems and networks to detect weaknesses that attackers could exploit to gain unauthorized access to systems or networks. Vulnerability scan is key in vulnerability management, which aims to protect your organization from data exposure and breaches.
Vulnerability scanning service is used for identifying and evaluating security flaws in applications and underlying systems and networks to detect weaknesses that attackers could exploit to gain unauthorized access to systems or networks. Vulnerability scan is key in vulnerability management, which aims to protect your organization from data exposure and breaches.
Performance
 Performance service includes performance characterization and benchmarking. The measurable quantitative qualities of the SaaS system, such as throughput, utilization, response time, and turnaround time will be measured to ensure the system meets user demands effectively. Periodical performance benchmarking will be done to establish a consistent feedback loop that can help optimize performance and efficiency.
Performance service includes performance characterization and benchmarking. The measurable quantitative qualities of the SaaS system, such as throughput, utilization, response time, and turnaround time will be measured to ensure the system meets user demands effectively. Periodical performance benchmarking will be done to establish a consistent feedback loop that can help optimize performance and efficiency.
High Availability
 was designed to handle different loads and failures with minimal or no downtime, so that users can access the system at any time without significant interruptions and application failover has been set up to ensure 99.99% availability.
was designed to handle different loads and failures with minimal or no downtime, so that users can access the system at any time without significant interruptions and application failover has been set up to ensure 99.99% availability.
Real-time Monitoring
 Real-time monitoring service is to provide the continuous analysis and reporting of data or events as they happen. It can help detect issues and respond to them as they occur, which can minimize downtime and improve user experience.
Real-time monitoring service is to provide the continuous analysis and reporting of data or events as they happen. It can help detect issues and respond to them as they occur, which can minimize downtime and improve user experience.
 Real-time monitoring can help in different contexts, including application performance and identification of potential issues to ensure that the applications are running smoothly.
Real-time monitoring can help in different contexts, including application performance and identification of potential issues to ensure that the applications are running smoothly.
Helpdesk
 provides a centralized service desk that helps our customers with technical issues and inquiries. Helpdesk is staffed by knowledgeable professionals who can provide guidance, troubleshoot issues, and offer solutions. The end users of our customers can inquire any questions related to
provides a centralized service desk that helps our customers with technical issues and inquiries. Helpdesk is staffed by knowledgeable professionals who can provide guidance, troubleshoot issues, and offer solutions. The end users of our customers can inquire any questions related to  and report incidents and problems.
and report incidents and problems.
Bug Fix
 bug-fix service includes reproducing the specific bug as reported, making sure the changes are properly tested, performing configuration management and change management to ensure the change is managed systematically, conducting release engineering and installing patches to the production system.
bug-fix service includes reproducing the specific bug as reported, making sure the changes are properly tested, performing configuration management and change management to ensure the change is managed systematically, conducting release engineering and installing patches to the production system.
DBA Service
 DBA service includes database installation, configuration, maintenance, backup, recovery, and performance optimization.
DBA service includes database installation, configuration, maintenance, backup, recovery, and performance optimization.
Backup
 Backup service includes weekly full backups and daily incremental backups and the backup files stored both on local and remote storage.
Backup service includes weekly full backups and daily incremental backups and the backup files stored both on local and remote storage.
Capacity Planning
 Capacity planning involves evaluating and forecasting the needs for hardware resources, storage and network bandwidth to ensure the system can handle expected loads and future growth.
Capacity planning involves evaluating and forecasting the needs for hardware resources, storage and network bandwidth to ensure the system can handle expected loads and future growth.
Disaster Recovery
 Disaster recovery service includes quickly restoring system functionality and data through predefined plans and procedures in the event of a system failure or disaster, ensuring business continuity.
Disaster recovery service includes quickly restoring system functionality and data through predefined plans and procedures in the event of a system failure or disaster, ensuring business continuity.
 standard SaaS disaster recovery service has the following objectives:
standard SaaS disaster recovery service has the following objectives:
- Recovery Point Objective (RPO) is less than 8 hours
- Recovery Time Objective (RTO) is less than 8 hours
Application Customization
 Advanced SaaS allows application customizations provided by us or done by our customers using
Advanced SaaS allows application customizations provided by us or done by our customers using  SDK. The types of customizations can range from development of interfaces to external systems, minor customization for changing
SDK. The types of customizations can range from development of interfaces to external systems, minor customization for changing  application behaviors to major customization such as adding new application modules to
application behaviors to major customization such as adding new application modules to  .
.
Web Accelerator
 Web Accelerator relies on BGP bandwidth and the global transmission network to achieve local access to the global network, which can reduce the impact of network problems such as latency, jitter, and packet loss on service quality, and provide high-availability and high-performance network acceleration services to global users.
Web Accelerator relies on BGP bandwidth and the global transmission network to achieve local access to the global network, which can reduce the impact of network problems such as latency, jitter, and packet loss on service quality, and provide high-availability and high-performance network acceleration services to global users.
Hardware Hot Failover
The system design of  Advanced SaaS allows adding extra hardware as hot standby to compensate for hardware failures. The goal is to ensure that
Advanced SaaS allows adding extra hardware as hot standby to compensate for hardware failures. The goal is to ensure that  Advanced SaaS remains functional and avoid downtime because of network equipment, server hardware or storage hardware failure.
Advanced SaaS remains functional and avoid downtime because of network equipment, server hardware or storage hardware failure.
 Advanced SaaS allows adding extra hardware as hot standby to compensate for hardware failures. The goal is to ensure that
Advanced SaaS allows adding extra hardware as hot standby to compensate for hardware failures. The goal is to ensure that  Advanced SaaS remains functional and avoid downtime because of network equipment, server hardware or storage hardware failure.
Advanced SaaS remains functional and avoid downtime because of network equipment, server hardware or storage hardware failure.
Short Recovery
 Short Recovery (RPO & RTO) means that in the event of a disaster,
Short Recovery (RPO & RTO) means that in the event of a disaster,  Advanced SaaS can recover more quickly and minimize data loss, making it suitable for businesses that need high business continuity and high data integrity.
Advanced SaaS can recover more quickly and minimize data loss, making it suitable for businesses that need high business continuity and high data integrity.
 Advanced SaaS has the following recovery objectives:
Advanced SaaS has the following recovery objectives:
- Recovery Point Objective (RPO) is less than 4 hours
- Recovery Time Objective (RTO) is less than 4 hours
IaaS & PaaS
 Infrastructure as a Service (IaaS) provides on-demand access to the basic building blocks of cloud IT, such as networking, storage, and virtual or dedicated hardware computers.
Infrastructure as a Service (IaaS) provides on-demand access to the basic building blocks of cloud IT, such as networking, storage, and virtual or dedicated hardware computers.
 Platform as a Service (PaaS) provides hardware and software resources, such as an operating system,
databases, programming language execution environment, web server running and managing
applications.
Platform as a Service (PaaS) provides hardware and software resources, such as an operating system,
databases, programming language execution environment, web server running and managing
applications.
Firewall
 Firewall monitors and controls network traffic to prevent unauthorized access to your computer or network. It acts as a barrier between your network and an untrusted outside network. Web Application Firewall (WAF) is a security defense that protects websites, mobile applications, and APIs from threats by monitoring, filtering, and blocking data packets. WAF was designed to detect and protect against common security flaws in web traffic. It can help protect against malicious attacks and unwanted internet traffic, including bots, injection, and application-layer Denial of Service (DoS).
Firewall monitors and controls network traffic to prevent unauthorized access to your computer or network. It acts as a barrier between your network and an untrusted outside network. Web Application Firewall (WAF) is a security defense that protects websites, mobile applications, and APIs from threats by monitoring, filtering, and blocking data packets. WAF was designed to detect and protect against common security flaws in web traffic. It can help protect against malicious attacks and unwanted internet traffic, including bots, injection, and application-layer Denial of Service (DoS).
Additional Security
Hypertext transfer protocol secure (HTTPS) is used to protect data transfer between a user and your server by encrypting all data in transit. This is especially important when users are transmitting sensitive data, such as personal and financial information. HTTPS ensures that no third parties can intercept the data over the network, and that the data has not been tampered with or modified.
 Two-factor authentication (2FA) is used as an identity and access management security method that requires two forms of identification to access resources and data.
Two-factor authentication (2FA) is used as an identity and access management security method that requires two forms of identification to access resources and data.  2FA gives your business and operations the ability to monitor and help safeguard their most vulnerable information and networks.
2FA gives your business and operations the ability to monitor and help safeguard their most vulnerable information and networks.
Advanced Encryption Standard (AES) 256 is used for file and database encryptions, Secure Hash Algorithm (SHA) 256 is used for password hashing and Pretty Good Privacy (PGP) 4096 is used for license file encryptions.
Certification
ISO27001 is an international standard that helps establish, maintain, and improve information security management systems (ISMS). The ISMS is a set of policies and procedures that outline how an organization's processes protect its data. The standard is used by companies of all sizes and from all sectors of activity.
ISO9001 is defined as a set of international standards on quality management and quality assurance developed to help organizations manage quality and ensure they meet customer expectations.
ISO9001 is defined as a set of international standards on quality management and quality assurance developed to help organizations manage quality and ensure they meet customer expectations.
Application Installation
 Application installation service includes installation and testing of the applications, middleware and proxy servers to make them ready for execution.
Application installation service includes installation and testing of the applications, middleware and proxy servers to make them ready for execution. Application installation service also include middleware and application version upgrades and patch installations for applications, proxy servers, middleware, DBMS and OS.
Application installation service also include middleware and application version upgrades and patch installations for applications, proxy servers, middleware, DBMS and OS.
OOTB Data Initialization
 OOTB data initialization service includes initialization of all the default code tables, policies and flows so that the system administrator can further customize them for specific needs.
OOTB data initialization service includes initialization of all the default code tables, policies and flows so that the system administrator can further customize them for specific needs.
Vulnerability Scan
 Vulnerability scanning service is used for identifying and evaluating security flaws in applications and underlying systems and networks to detect weaknesses that attackers could exploit to gain unauthorized access to systems or networks. Vulnerability scan is key in vulnerability management, which aims to protect your organization from data exposure and breaches.
Vulnerability scanning service is used for identifying and evaluating security flaws in applications and underlying systems and networks to detect weaknesses that attackers could exploit to gain unauthorized access to systems or networks. Vulnerability scan is key in vulnerability management, which aims to protect your organization from data exposure and breaches.
Performance
 Performance service includes performance characterization and benchmarking. The measurable quantitative qualities of the SaaS system, such as throughput, utilization, response time, and turnaround time will be measured to ensure the system meets user demands effectively. Periodical performance benchmarking will be done to establish a consistent feedback loop that can help optimize performance and efficiency.
Performance service includes performance characterization and benchmarking. The measurable quantitative qualities of the SaaS system, such as throughput, utilization, response time, and turnaround time will be measured to ensure the system meets user demands effectively. Periodical performance benchmarking will be done to establish a consistent feedback loop that can help optimize performance and efficiency.
High Availability
 was designed to handle different loads and failures with minimal or no downtime, so that users can access the system at any time without significant interruptions and application failover has been set up to ensure 99.99% availability.
was designed to handle different loads and failures with minimal or no downtime, so that users can access the system at any time without significant interruptions and application failover has been set up to ensure 99.99% availability.
Real-time Monitoring
 Real-time monitoring service is to provide the continuous analysis and reporting of data or events as they happen. It can help detect issues and respond to them as they occur, which can minimize downtime and improve user experience.
Real-time monitoring service is to provide the continuous analysis and reporting of data or events as they happen. It can help detect issues and respond to them as they occur, which can minimize downtime and improve user experience.
 Real-time monitoring can help in different contexts, including application performance and identification of potential issues to ensure that the applications are running smoothly.
Real-time monitoring can help in different contexts, including application performance and identification of potential issues to ensure that the applications are running smoothly.
Helpdesk
 provides a centralized service desk that helps our customers with technical issues and inquiries. Helpdesk is staffed by knowledgeable professionals who can provide guidance, troubleshoot issues, and offer solutions. The end users of our customers can inquire any questions related to
provides a centralized service desk that helps our customers with technical issues and inquiries. Helpdesk is staffed by knowledgeable professionals who can provide guidance, troubleshoot issues, and offer solutions. The end users of our customers can inquire any questions related to  and report incidents and problems.
and report incidents and problems.
Bug Fix
 bug-fix service includes reproducing the specific bug as reported, making sure the changes are properly tested, performing configuration management and change management to ensure the change is managed systematically, conducting release engineering and installing patches to the production system.
bug-fix service includes reproducing the specific bug as reported, making sure the changes are properly tested, performing configuration management and change management to ensure the change is managed systematically, conducting release engineering and installing patches to the production system.
DBA Service
 DBA service includes database installation, configuration, maintenance, backup, recovery, and performance optimization.
DBA service includes database installation, configuration, maintenance, backup, recovery, and performance optimization.
Backup
 Backup service includes weekly full backups and daily incremental backups and the backup files stored both on local and remote storage.
Backup service includes weekly full backups and daily incremental backups and the backup files stored both on local and remote storage.
Capacity Planning
 Capacity planning involves evaluating and forecasting the needs for hardware resources, storage and network bandwidth to ensure the system can handle expected loads and future growth.
Capacity planning involves evaluating and forecasting the needs for hardware resources, storage and network bandwidth to ensure the system can handle expected loads and future growth.
Disaster Recovery
 Disaster recovery service includes quickly restoring system functionality and data through predefined plans and procedures in the event of a system failure or disaster, ensuring business continuity.
Disaster recovery service includes quickly restoring system functionality and data through predefined plans and procedures in the event of a system failure or disaster, ensuring business continuity.
 standard SaaS disaster recovery service has the following objectives:
standard SaaS disaster recovery service has the following objectives:
- Recovery Point Objective (RPO) is less than 8 hours
- Recovery Time Objective (RTO) is less than 8 hours